Using veracrypt I encrypt my entire OS, when I power on my pc I need to first decrypt the entire os, I enter a password between 15-25 digits long and a key file on separate USB, if you steal my hard drive all you will see is gibberish nonsense. Veracrypt is as good as an encryption software can get giving you the ability to choose from common public tested and verified encryption protocols. It may seem like paranoia but all my data is encrypted on a flash disk or any other way I do not have openly readable files to me that seems careless its like locking your house and leaving the store door unlocked, yeah it takes time to decrypt but to me data security is a top priority.
When you call encryption primitive I almost laughed my ass off, encryption is the best thing we have in terms of data protection any other thing from that is human error(weak passwords, publicly storing encryption keys e.t.c) and you can not zero day an encryption, bitlocker is a mass produced software for non -It folks obviously bugs zitakua in-fact in earlier versions you could power down the pc access your hard drive through another pc and access the master encryption keys in a clear file(it was fixed kitambo tho)
Sure you can capture packets from a WIFI network protected with wep encryption and crack it if it had a simple pass phrase like jostokubwawifi, on the other hand according to my pc(And my pc is a beast) cracking my wifi password(qwe#tvd%hhs&nxi.)cd^() will take me 50 years.
encryption is used on everything.
1)when you make a phone call you use End-to-end call encryption (E2EE) hence I can not snoop in. by the way the decryption key is stored on your sim card and is some combo of your phone number and imei
2)when you access a webserver/webpage you use https for encryption
3)when you connect to a wifi network you use wpsk/wep
If encryption is cracked technology will be useless as anyone with any kind of technical knowledge can view anything in the wires or air(passwords, bank account details, government secrets e.t.c
oh and a btw
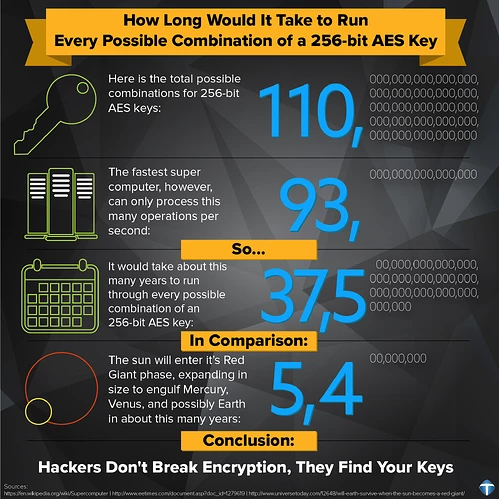
How long does AES-256 take to crack?
With the right quantum computer, AES-128 would take about 2.6110^12 years to crack, while AES-256 would take 2.2910^32 years. For reference, the universe is currently about 1.38×10^10 years old, so cracking AES-128 with a quantum computer would take about 200 times longer than the universe has existed.
Now if you said rainbow tables that would have made sense to crack passwords which saves time by costing memory(lots of memory, am not joking am talking people have 500TB+ rainbow tables in size)